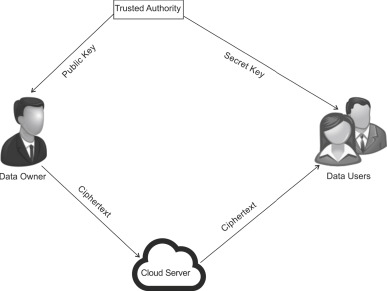
In an age where data breaches and cyber-attacks are becoming more sophisticated, traditional encryption methods often fall short in providing the fine-grained control needed to secure sensitive information. Attribute-Based Encryption (ABE) offers a novel approach to data encryption that is transforming how we manage and secure data, especially in cloud storage and the Internet of Things (IoT).
Unlike traditional encryption methods, where a user with a decryption key gains full access to the data, ABE enables encryption based on attributes or policies. This means that access to encrypted data is controlled by the attributes of the user, such as their role, department, or clearance level, and the access policy set by the data owner. This fine-grained control makes ABE particularly well-suited for multi-user environments where different users require different levels of access to the same data.
One of the key applications of ABE is in cloud storage, where organizations store vast amounts of sensitive data that need to be accessed by multiple users. In a traditional encryption system, each user would need a different key to decrypt the data they are authorized to access, leading to significant overhead in key management. ABE simplifies this process by allowing the data owner to set an access policy that defines which users can decrypt the data based on their attributes. This reduces the need for managing multiple encryption keys and ensures that only authorized users can access sensitive data.
For example, in a healthcare system, patient records could be encrypted using ABE, with access granted to doctors, nurses, and insurance agents based on their roles. A doctor might have full access to the patient’s medical history, while a nurse may only have access to specific records, and an insurance agent may only be able to view billing information. This level of access control ensures that sensitive medical information is protected while still allowing authorized users to access the data they need.
In the Internet of Things (IoT), ABE provides a solution for securing communication between devices. As IoT networks grow, managing access to encrypted data becomes increasingly challenging. With ABE, devices can be granted access to encrypted data based on their attributes, such as their location, type, or security clearance. This ensures that only authorized devices can access sensitive information, reducing the risk of data breaches from compromised or unauthorized devices.
Another significant advantage of ABE is its resilience to insider threats. In traditional encryption systems, if an insider gains access to the decryption key, they can access all the encrypted data. However, with ABE, even if an insider gains access to a key, they can only decrypt the data they are authorized to access based on their attributes. This adds an extra layer of security, making it more difficult for insiders to access sensitive information.
As data security becomes increasingly important in today’s digital landscape, ABE is poised to play a critical role in the future of encryption. Its ability to provide fine-grained access control makes it an ideal solution for cloud storage, IoT networks, and any environment where multiple users need access to encrypted data.