Random number generators (RNGs) are a foundational element of modern cryptography, essential for generating encryption keys, digital signatures, and other cryptographic protocols that secure communications and data. While random numbers might seem trivial, the strength of cryptographic systems heavily depends on the quality of randomness generated. Poorly designed RNGs can lead to serious vulnerabilities that undermine the entire encryption process, as was seen in the infamous 2008 Debian OpenSSL vulnerability.
In cryptography, randomness is crucial for ensuring that encryption keys and other sensitive data cannot be predicted by attackers. If an RNG is weak or predictable, it can open the door for hackers to reverse-engineer encryption keys, compromising the security of the system. This makes RNGs a critical component in the development of secure cryptographic systems.
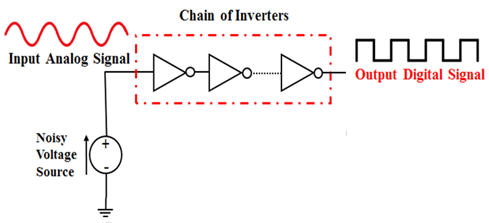
There are two primary types of random number generators used in cryptography: true random number generators (TRNGs) and pseudo-random number generators (PRNGs). TRNGs rely on physical processes, such as radioactive decay or thermal noise, to generate genuinely random numbers. While TRNGs offer the highest level of randomness, they tend to be slower and more expensive to implement than PRNGs. PRNGs, on the other hand, use mathematical algorithms to generate sequences of numbers that appear random but are actually deterministic. The key to a secure PRNG lies in its unpredictability—an attacker should not be able to predict future outputs based on past numbers.
The security of cryptographic systems depends on ensuring that PRNGs are properly seeded with high-entropy data. A poorly seeded PRNG can result in predictable outputs, which makes it easier for attackers to break the encryption. This is why cryptographic standards, such as those published by NIST and the International Organization for Standardization (ISO), provide guidelines for implementing secure RNGs and testing their quality.
RNGs are used in various cryptographic applications, from generating encryption keys and digital signatures to securing communication protocols like SSL/TLS and blockchain-based systems. For example, in blockchain, RNGs are essential for creating unique transaction IDs and ensuring the integrity of consensus mechanisms. Similarly, in secure communication protocols, RNGs are used to generate session keys that protect the confidentiality and integrity of data exchanges.
As quantum computing continues to advance, the role of RNGs in cryptography becomes even more critical. Quantum computers have the potential to break traditional encryption methods like RSA and ECC by solving the underlying mathematical problems much faster than classical computers. In response, post-quantum cryptography is emerging as a new field that aims to develop cryptographic algorithms resistant to quantum attacks. Strong, secure RNGs will be essential for generating the cryptographic keys used in these new systems.
In conclusion, RNGs are a vital component of cryptographic security. Ensuring that these generators produce high-quality, unpredictable randomness is essential for the security of modern digital systems. As technology continues to evolve, the importance of RNGs in safeguarding the digital future cannot be overstated.